A new variant of the DirtJumper malware has been discovered that is capable of launching even more powerful distributed denial-of-service attacks.
Dubbed “Drive” by researchers, the new variant is part of the DirtJumper family and has a new and much more powerful DDoS engine and new attack features and commands, Jason Jones, a research analyst at Arbor Networks, wrote on the Arbor Security Engineering and Response Team (ASERT) blog on Thursday. A few command-and-control servers have already been observed serving up Gzip compressed data, and at least one is using geography-based blocking, Jones said.
The team behind Drive has been “ambitious,” as it has already been used to target a “popular online retailer, search engine, a popular security news site, and some foreign financial institutions,” Jones said. Some attacks were successful, but some were not.
“Drive is an up-and-coming threat on the ASERT radar and something we will continue to monitor closely in the coming months as it continues to spread and attack new targets,” Jones said.
 The new variant is a sign the team behind DirtJumper has changed its attack methods to include more potent capabilities in the next generation of DDoS tools. However, this new variant does not appear to have made it to the mainstream underground forums yet, Jones said. Only 15 C&C hostnames have been observed so far.
The new variant is a sign the team behind DirtJumper has changed its attack methods to include more potent capabilities in the next generation of DDoS tools. However, this new variant does not appear to have made it to the mainstream underground forums yet, Jones said. Only 15 C&C hostnames have been observed so far.
One of the observed C&C machines was co-hosting on the same server as a BetaBot C&C and a BitCoin mining harvester, Jones said. All three appear to have been dropped by SmokeLoader. Another C&C, which was targeting foreign financial institutions, was difficult to monitor because it blocked all connections which did not originate from a specific geographic location.
Depending on the C&C, Drive was making 1,000 to 2,000 queries at the height of the attack.
While Drive has code to handle instructions to attack secured Websites, “we have not seen any copies of Drive that have an embedded SSL library to actually support an attack over HTTPS,” Jones said.
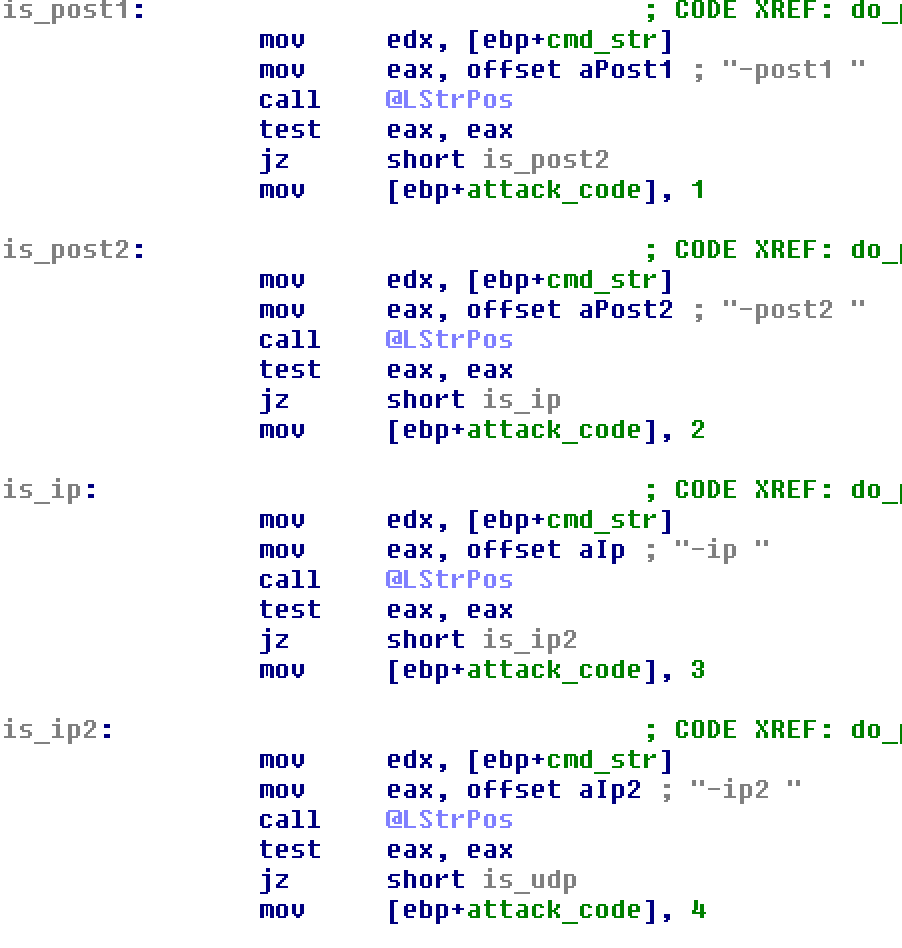
Drive sports 2 POST floods, a GET flood, 2 connection and data floods and a UDP flood–although the UDP flood was not seen in all instances, Jones said.
Drive can also specify the post query string of random data. If the attackers are targeting login or search pages on the server, this customized string can cause additional stress on the system.
Drive also has a new string encryption algorithm to encrypt all “sensitive” data, including the V&V host, C&C port, C&C URI, installation name, and the .INI name. The format of the command string used to send instructions about what servers to attack and what kind of attacks to launch has also changed. It can also specify a timeout, the number of threats to launch, and launch a mix of attack types.
Along with modifying the User Agent string, Drive can also launch connection-style flood attacks containing randomly generated data to the ports for HTTPS, SSH, and MySQL (to name a few), on the targeted server. The UDP flood “is a pretty standard UDP flood,” and has only been seen a handful of times from the C&C servers, Jones said.
“The attacks we have witnessed have proved to be more potent than other variants,” Jones said.
















