Experienced Security Teams Know that Every Piece of Malicious Software Cannot be Caught in Advance
Over the past five years, there have been multiple new entrants into the endpoint protection space, looking to provide better defenses against increasingly subtle and sophisticated malware.
New players are driving a reexamination of protection strategies, and new approaches are vying for dominance. Legacy antivirus systems that rely on scanning, sometimes shorthanded to “traditional antivirus”, are still widely deployed, but enhancements to that approach now include heuristic analysis and predictors informed by machine-learning across millions of samples. Recognizing that security is never foolproof, (and oftentimes we users are the fools,) there are multiple solutions that can recognize the damage that malware causes, so that organizations can recognize infected systems before malware further infests their networks. For the security lead or IT director in charge of protection, the similarities and claimed differences are muddled and confusing.
Organizational cybersecurity usually relies on a series of protective layers, representing the well-worn “defense-in-depth” approach. Now that there are so many options, endpoint security is best thought of similarly, with threats acting along a timeline. Security measures should be applied in a balanced way across this malware lifecycle, to maximize the effectiveness of the defense. Given the nature of the risk and attack vectors, it is clearest to think about the challenge in three stages:
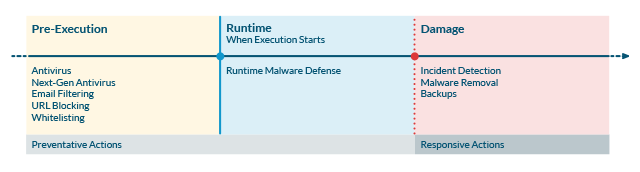
• Pre-execution Malware Defense: Identify and eliminate malware before it can execute
• Runtime Malware Defense: Identify and block malware before it can cause damage
• Malware Detection & Removal: Identify malware infections to reduce dwell time and damage
Maximizing Protection at the Endpoint
For the security manager or harried IT-Pro, implementing this kind of protection requires understanding the role that vendor solutions can play in each of these three phases.
Pre-Execution Comes First
Whenever we look at attacks, whether in their initialization or their dwell time, it is best to find them early. As a result, pre-execution malware defense is the logical place to start. In earlier years, when malware was less common, and wasn’t specifically written to avoid detection, scanning techniques, whitelists, and blacklists arose to block undesirable software from reaching systems or being accessed there. So long as the number of unique samples was manageable, this system was adequate, and bad malware was blocked before it could execute.
In only a decade or so, though, malware had transformed. Recognizing that individual packages were being identified and blocked, malware writers first created automated means of generating thousands of variants of each of their attack packages, and then ultimately created packages which would generate themselves anew on every machine they found. This put the idea of a comprehensive list of bad software out of reach, and caused the cat and mouse latency chase that affects so many signature and scanning based incumbents.
Thus arose new pre-execution identification techniques that were less dependent upon the construction and content of the individual executable, and that relied on identifying characteristics of malicious executables that were common across multiple malware families. In many cases new versions of existing executables were caught this way, in scans and at access time, and Next-Generation AV (NGAV) was born. It has the capability of identifying families of descendants from known malware, but it it cannot recognize attacks that are truly novel, or that never organize themselves into objects that can be scanned and analyzed in this way.
Runtime Malware Defense
As a result, real protection requires some additional investment before giving up and waiting for detection technologies to give their bad news. The defining characteristic of strong runtime malware defense is the ability to recognize unique behaviors of malicious software before it can cause any damage. Assuming that either traditional or next-generation anti-virus solutions are doing their jobs pre-execution, the runtime solution has to be able to catch all of the newest attacks and the streaming or transient software that is trying to execute on the victim system. This is a very new area, with the new solutions coming to the market at almost the same time as the new attacks which are developed to avoid the earlier protection strategies.
Evaluating these new solutions should resemble the internal analysis of endpoint protection as an area. How early can the solution identify the malicious behavior, and how broad are the types of behaviors that it can see? Good examples include malicious process creation, resource manipulation, exploit techniques, and privilege escalation. Identifying malicious software by recognizing that it just damaged the system or exfiltrated some amount of information is no longer defense, but detection.
Malware Detection
Good malware detection is still valuable, as there will always be some threat, or some combination of user error and system configuration, that manages to create an opening. When this happens, early detection can be the difference between restoring a backup and filing for a breach notification. Detection comes in many forms, from network and host-based anomaly detection to SIEM analytics to recognizing static indicators of compromise. Once these are seen, early notification and plans for interdiction and clean-up make the damage as limited and short-lived as possible.
Aside from anti-virus solutions, this kind of monitoring, detection, and recovery, has benefitted most from years of development, deployment, and retooling. There is substantial available documentation on best practices, and well-established solution and service providers to help out.
Security Value for the Next Dollar
Pre-execution malware defenses and later malware detection are well-established areas of investment in most firms, even if that only means investment in anti-virus and a logfile notification service. The current most vulnerable area, responding to the newest and most successful threats, is in the middle, at runtime. Experienced security teams know that every piece of malicious software cannot be caught in advance, and they know that cleaning up after an event is painful and often incomplete. As a result, runtime malware defense is the next area of hardening that will be seeing investment by both security solution providers and their customers. The intelligence of the attackers has forced a change in the pr
oblem space: New protection needs to stop the malicious behavior because it cannot always find or recognize the malicious package.
















