An impression fraud scheme powered by a piece of malware that has infected millions of devices could cost advertisers a lot of money, enterprise analytics and security company Pixalate warned on Wednesday.
The Xindi Botnet
The malware, dubbed by Pixalate “Xindi,” is designed to infect computers and abuse them to generate fake “viewable” impressions. The threat, discovered by the security firm in July, is delivered via drive-by downloads, other malware, and phishing attacks, and it’s believed to have infected 6-8 million machines housed by more than 5,000 organizations, including Fortune 500 companies, 1,500 universities, and over 200 financial and government institutions.
Experts believe the attackers have targeted the networks of these types of organizations to take advantage of their large bandwidth, computing power, and good reputation. In the United States, the highest number of Xindi infections have been spotted in California (12%), New York (8%), Texas (7%) and Florida (7%).
The Xindi botnet, which Pixalate says it’s a first of its kind, is designed to exploit a flaw in the implementation of the OpenRTB communication protocol to help cybercrooks conduct impression fraud.
According to Pixalate, traffic patterns resembling the Xindi botnet were first spotted in October 2014, with other attacks observed in December 2014, March 2015 and August 2015. The company estimates that if the problem is not dealt with, the Xindi botnet could cost advertisers as much as $3 billion by the end of 2016. The list of affected advertisers includes Home Depot, Uber, McDonald’s, Honda, Verizon, Monster and Nissan.
Impression Fraud Scheme
Real-time bidding (RTB) is a system that allows online advertising buyers to bid on an ad impression in real-time. The winning buyer’s ad is instantly displayed on the publisher’s website.
OpenRTB, a project of Interactive Advertising Bureau (IAB), is an open standard designed to facilitate communication between buyers of advertising and sellers of publisher inventory.
In a normal OpenRTB flow, when a user visits a publisher’s website, their browser sends an ad request to the supply-side platform (SSP) or ad exchange, which in turn broadcasts bid requests to multiple demand-side platforms (DSPs), systems that allow ad buyers to manage multiple ad exchange accounts through a single interface.
The DSP sends the bid responses to the SSP, which sends an ad back to the browser for rendering. Once the ad is rendered, notifications are sent to the SSP and the DSP, and the ad is displayed to the user.
In the case of the Xindi botnet, the malware sends ad requests to the SSP by silently launching a session in the browser. The process is repeated multiple times, but the ad markups are not rendered and instead are hoarded in a transient state for a period of time ranging between a few seconds to a few hours.
Finally, Xindi replays the ad markups it had been hoarding in a burst and only then the ad render notifications are sent to the SSP and DSP.
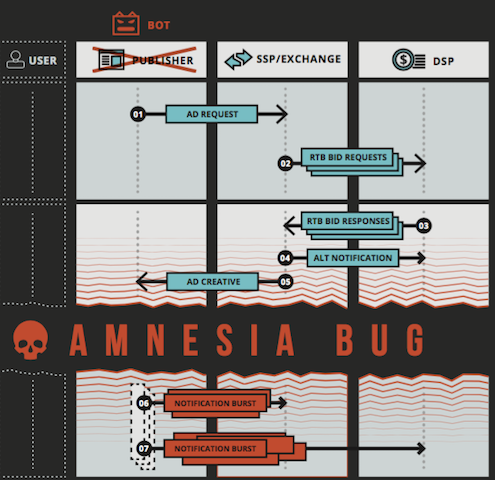
This attack technique is made possible by an OpenRTB implementation issue, which allows fraudsters to conceal the true status of an ad transaction. By hiding the status, the bidding engine bids on a larger number of impressions for each compromised host than originally intended, which results in the fraudsters making a profit.
“In active campaigns the botnet was found to increase fraud by up to 300% and to consistently falsify viewability by up to 90%,” Pixalate said in its report.
The Amnesia Bug
Pixalate says the Xindi botnet abuses a vulnerability in the OpenRTB 2.3 protocol implementation, which the company has dubbed the Amnesia Bug (CVE-2015-7266). The problem, according to researchers, is that OpenRTB does not define maximum time limits that would prevent delayed bursts of fraudulent impressions.
IAB representatives say the problem is not with the OpenRTB protocol.
“The problem is not with the OpenRTB protocol. Challenges can arise with implementation of systems that use protocols such OpenRTB, and others, at the individual company level. We see vulnerabilities appear due to how some business build their operations, rather than issues with a protocol itself,” Scott Cunningham, General Manager of the IAB Tech Lab, told SecurityWeek. “To encourage proper use, IAB Working Groups update implementation best practices on a ongoing basis. And frankly, this is why TAG was established. Know what trusted parties to buy from.”
Additional technical details and mitigation advice is available in Pixalate’s report.








