Hackers looking to steal sensitive data, such as intellectual property, deal data or PII, know exactly where to find it: in the databases, file servers, and applications that comprise an organization’s data center. Therefore the ultimate and unchanging goal of hackers is to get into the datacenter. While the goal remains constant, the means hackers use to get their hands on data keeps evolving. In this column we will explore the recent trend of hackers abusing the target’s Web application in order to launch an attack on the datacenter.
Hackers Modus Operandi
Hackers apply a very methodical approach to get into the datacenter. They first establish a bridgehead within the target’s network by infecting a computer within the network. Once this foothold is established and secured, the hackers start moving laterally within the target’s network, usually by obtaining users’ credentials, to get from that bridgehead, which might be located in an arbitrary workstation, to a strategic point that has access to the datacenter. Finally, datacenter is accessed and exfiltrated data is sent back to the hacker.
Hackers, very much like any other company in a competitive market situation, are constantly striving to improve their process. The later stages of the hacking process, i.e. data gathering from the datacenter and exfilitration, are intrinsic to it and thus cannot change fundamentally, as the data resides on the datacenter and the hacker resides on the internet. However, the former stages are just a means to an end and therefore are more suitable for innovation.
The evolution of the bridgehead
The traditional method for hackers to establish a malicious bridgehead inside of the victim’s corporate network is through the infection of the corporate’s end users. The user is usually targeted through a dedicated phishing email, which contains malware infecting attachments or link to an infecting Website.
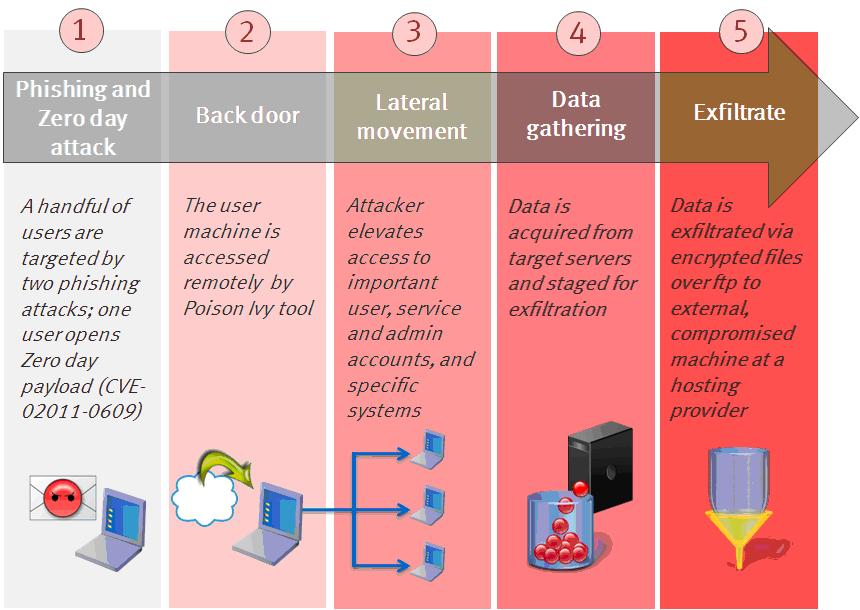
An Anatomy of a Classic Attack (Image Credit: RSA)
However, by analyzing recently reported cases such as the Bit9 hacking, attackers had taken a novel approach. The Bit9 hackers’ had constructed the malicious bridgehead not on a user’s endpoint but on the corporate’s Web server. Attacker had exploited an SQL injection vulnerability in the Web application to install the HiKit malware. Using the HiKit over the Web server bridgehead the hackers were able to eventually get to datacenter and achieve their goal of abusing Bit9’s code signing certificates.
Why are attackers moving from phishing to Web applications attacks as a method to create the desired bridgehead en route to the datacenter?
There are at least four good reasons to it:
1. Removing the human factor: Experience shows that attackers will succeed in infecting one of the corporate users through phishing, eventually. However, this penetration course is based on social engineering and therefore has some manual and target specific aspects to it; In order to make the victim actually read the email and click the infecting link or attachment, an appealing and credible message needs to be crafted. Since “appealing” and “credible” are in the eyes of the beholder and varies on the specific user it often requires a substantial amount of manual labor. Naturally, manual labor is an undesired effect, as hackers (again, very much like any other industry) strive for automation in order to reduce costs and achieve more timely results. In comparison, attacks on the Web application consist on technical vulnerabilities abuse without any social engineering aspects to it and therefore can be fully automated.
2. Landing near target: The classic penetration with phishing method lands the attacker code in an arbitrary location within the target’s network. If this bridgehead happens to be very far from the datacenter it means that the lateral movement stage will take a lot of time. Sometimes the attacker infect totally irrelevant targets as the victims had read the phishing mail on their home computer which is not connected to the corporate network. In contrast, the Web server is usually located within the datacenter or just one hop away, making the lateral movement stage very rapid or even completely unnecessary.
3. Allowing direct communications: Firewalls protect endpoints within the corporate network against direct, real time access from the internet. Therefore, attackers need to use the indirect and asynchronous E-mail channel to smuggle its malicious payload to the end user. Additionally, once the endpoint gets infected with the malware, its Command and Control (C2) server cannot send commands directly, but needs to wait for the malware to call back home to initiate contact. In contrast, Web servers are open to incoming communication by definition, therefore both initial infection and following C2 communication can be conducted in real-time, thus saving hackers some precious time.
4. Avoiding the opposition – the attackers way into the user endpoint is heavily guarded and landmined with all sorts of security obstacles: SPAM filters and Antivirus solutions embedded with the mail server, Antivirus solutions installed on endpoints and outgoing Web monitoring appliances (detecting C2 communications and malware download) deployed on the network. In comparison the Web server is usually only protected with a firewall or an IDS which cannot stop application layer attacks such as SQL injection.
Conclusions
What should the defensive side do to accommodate this novel penetration method of infiltrating the datacenter through the Web application? I believe there should be two immediate corollaries:
Focus on the datacenter: regardless of the penetration method, the endgame of the attacker is the datacenter. Therefore protecting the datacenter should be the paramount objective of the defensive side. Defense should make the protecting against the access of sensitive data from infected machine its number one priority at the expense of protecting against the changing ways the machine has become infected in the first place.
Rebalance the protection against initial penetration methods: While the traditional penetration method of infecting a user’s endpoint with malware is heavily defended with different security mechanism on the different layers levels, the Web application is often not shielded at all. The bare minimum to protect against penetration through the Web server is investing in relevant security measures such as deploying a Web Application Firewall (WAF) to protect it.













