Google informed bug bounty hunters on Thursday that it has made some changes to its Vulnerability Rewards Program (VRP), including offering more money for certain types of flaws.
Until now, the tech giant had offered $20,000 for remote code execution (RCE) vulnerabilities and $10,000 for unrestricted file system or database access issues. The rewards have now increased to $31,337 and $13,337, respectively.
Researchers can earn $31,337 if they find command injections, sandbox escapes and deserialization bugs in highly sensitive applications, such as Google Search, Accounts, Wallet, Inbox, Code Hosting, Chrome Web Store, App Engine, Google Play, and Chromium Bug Tracker. If the flaws affect non-integrated acquisitions or apps that have a lower priority, the maximum reward is $5,000.
The unrestricted file system or database access category includes unsandboxed XXE and SQL injection vulnerabilities. These types of flaws can earn bounty hunters up to $13,337 if they affect highly sensitive services.
Google also announced that rewards attributed to vulnerability reports from its internal web security scanner will be donated; $8,000 have been donated this year to rescue.org.
The company reported in late January that it has paid out more than $9 million since the launch of its bug bounty program in 2010, including $3 million awarded last year. More than $400,000 of the total amount paid out in 2016 represented rewards that exceeded $20,000, including a single reward of $100,000.
A survey conducted by Google among its top researchers showed that, in 2016, 57 percent of them looked for vulnerabilities a few times a month, nearly 24 percent looked rarely or never, and 19 percent put their skills to work almost every day. Half of the respondents said they sometimes found flaws, while 16.7 percent said they almost always found flaws. One-third of respondents said they very rarely or never discovered bugs.
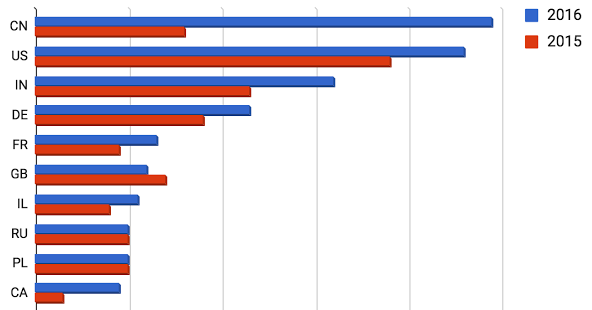
The highest numbers of researchers paid in 2016 were based in China, the United States and India.
Related: Google Increases Android Bug Bounty Payouts
Related: Google Pays $25,000 Reward for Critical Chrome Flaw
Related: Google Puts Up $1 Million for Security Research Grants












