Chinese Cyberspies Target Myanmar and Other Countries
A threat group believed to be affiliated with the Chinese government has been conducting cyber espionage operations against Myanmar and other countries for economic gain.
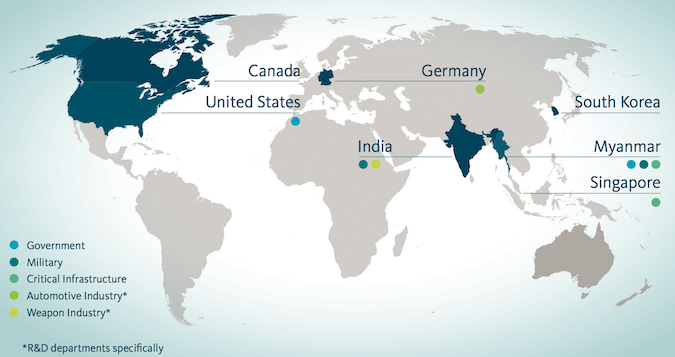
The actor, dubbed “Mofang” by Dutch security firm Fox-IT, has targeted entities in Myanmar, India, Germany, Canada, the United States, Singapore, South Korea and likely other countries since at least February 2012. The attacks have focused on government, military, critical infrastructure, automotive and weapons organizations.
Many of Mofang’s attacks targeted organizations in Myanmar, but one of the most recent campaigns against the country appears to show exactly what type of leverage a nation-state can gain by conducting cyberespionage.
The operation in question was related to Myanmar’s Kyaukphyu special economic zone (SEZ), where China’s National Petroleum Corporation (CNPC) had been investing since 2009 after signing a memorandum of understanding with the government.
In March 2014, the government of Myanmar announced that Singapore-based CPG Corporation had won a consulting tender that put it in charge of overseeing foreign investments in the Kyaukphyu SEZ. In the same year, CPG Corp. and the Myanmar government initiated another tender for setting up infrastructure in this SEZ, and in early 2016 it was announced that China’s CITIC group had won it.
Before CITIC was declared the winner, in mid-2015, Mofang was observed launching attacks against Myanmar government organizations and CPG Corp. Experts believe the information the hackers may have stolen from the targets could have helped the Chinese company win the tender.
Chinese cyberspies have often been accused of stealing information that would give the country a competitive advantage, but it’s not often that a specific cyberattack is tied to actual economic benefit for China.
Fox-IT has connected the Mofang attacks to a single group based on the tools that have been used. Unlike other threat groups, which often leverage exploits to infect their targets, Mofang has relied on social engineering to accomplish the task. The only exploits used by the APT were previously known privilege escalations built into their malware.
Mofang’s toolset consists of two main pieces of malware. One of them is a remote administration tool (RAT) dubbed ShimRat, which allows attackers to manipulate files and folders, upload and download files, and execute programs and commands.
Researchers determined that the development of ShimRat started in 2012 and the threat has been significantly improved over the past years. Similar to other China-based cyberspies, Mofang also uses antivirus hijacking techniques to run ShimRat.
The threat actor has also been using ShimRatReporter, a tool first spotted in late 2014. ShimRatReporter has been used to collect information about the targeted organization’s infrastructure, and to download a second stage payload – usually a customized ShimRat build.
While ShimRat has been known to security firms – some have even mistaken it for the PlugX RAT that is widely used by Chinese APTs – Yonathan Klijnsma, the lead author of Fox-IT’s report on Mofang, says no other security firms have conducted an in-depth investigation of the malware or the threat actor’s activities.
Related: US Charges Chinese Worker for IBM With ‘Economic Espionage’
















