A known cyber espionage group believed to be operating out of China was last year spotted using new malware in an attack aimed at an organization that provides services to the U.K. government.
Details about the attack were presented last week at Kaspersky’s Security Analyst Summit (SAS) in Cancun by Ahmed Zaki, senior malware researcher at NCC Group.
The attack has been attributed to a threat actor known as APT15, Ke3chang, Mirage, Vixen Panda and Playful Dragon. NCC Group started analyzing the group’s recent activities after it targeted one of its customers, a global company that provides a wide range of services to the United Kingdom government.
Researchers believe the attackers had been targeting various U.K. government departments and military technology through its customer. NCC has not made any statements regarding attribution, but Zaki did mention during his presentation at SAS that APT15 was particularly active during hours that correspond to working hours in East Asia.
APT15 has been active since at least 2010 and it has targeted organizations all around the world using its own malware and Word, Adobe Reader and Java exploits. The group has improved its tools and techniques over the years, and NCC recently spotted two new backdoors it created.
One of the backdoors has been dubbed RoyalCLI and is considered a successor of BS2005, a piece of malware that is often used by the group. RoyalCLI leverages similar encryption and encoding routines, and they both communicate with command and control (C&C) servers via Internet Explorer using the IWebBrowser2 interface.
The malware uses the Windows command prompt (cmd.exe) to execute a majority of its commands. It’s designed to copy the cmd.exe file and modify it, which allows it to bypass policies that might prevent the command prompt from running on the targeted device.
The second backdoor, named RoyalDNS, uses DNS, specifically TXT records, to communicate with the C&C server. This piece of malware receives commands, executes them, and returns output through DNS.
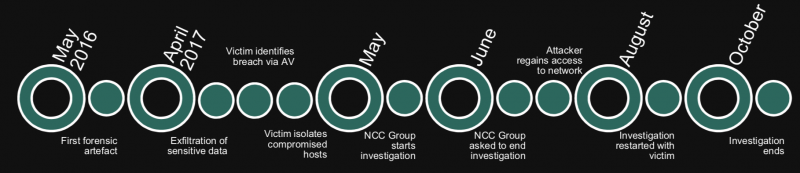
In the case of the attack analyzed by NCC, the hackers compromised more than 30 hosts, with forensic artifacts showing that the initial intrusion may have occurred as early as May 2016. NCC was asked by the client to stop its investigation in June 2017, but resumed it in August after the threat actor managed to regain access to the victim’s network. Experts determined that the hackers had stolen a VPN certificate from a compromised host and used it to regain access via the corporate VPN.
The commands sent by the attackers to the RoyalCLI and BS2005 malware were cached to the disk of compromised devices, allowing researchers to recover over 200 commands. Since one of the commands contained a typo, investigators determined that they were likely sent by a human operative rather than an automated process.
In addition to BS2005, RoyalCLI and RoyalDNS, APT15 used custom-built keyloggers, and Microsoft SharePoint and Exchange enumeration and data dumping tools. The group’s arsenal also includes widely available tools such as Mimikatz, CSVDE, NetEnum, and RemoteExec.
Moreover, the attackers relied on various Windows commands to conduct reconnaissance, including tasklist, ping, netstat, net, systeminfo, ipconfig and bcp. For lateral movement they leveraged the net command and manually copied files to and from compromised hosts.
“Through our investigation we were able to identify and monitor the attack process from start to finish, offering us unique insight into the behaviour of this group,” Zaki said. “It’s clear to see that this is a highly sophisticated threat actor that has no problem writing tools which are specific to its victims.”













