Last week, Microsoft released the latest Microsoft Security Intelligence Report (SIR), which provided some interesting empirical insight into malware and how it is distributed on the Internet. The headline of the SIR focused on the strong correlation between malware and downloads of software, music, and movies. That finding shouldn’t come as much of surprise to those in the security field, as unlicensed content and cracked software has been a mainstay of malware for years.
What was a bit more interesting was the data showing the broad impact of the Black Hole exploit kit in terms of its role in the delivery of threats. Black Hole is a very popular exploit kit that an attacker can use to build a malicious web page capable of infecting users who visit the page. Once the user is exploited, malware is delivered to the infected user as a drive-by-download. This scheme is the classic example of the inter-relationship between exploits and the spread of malware. Exploits soften up the target, which is then infected with malware, and all of it happens in real-time over a web connection.
Of course, this kit and technique are exceedingly well known in the industry, but it was interesting to see just how quickly it has become one of the dominant forces in the delivery of exploits and malware.
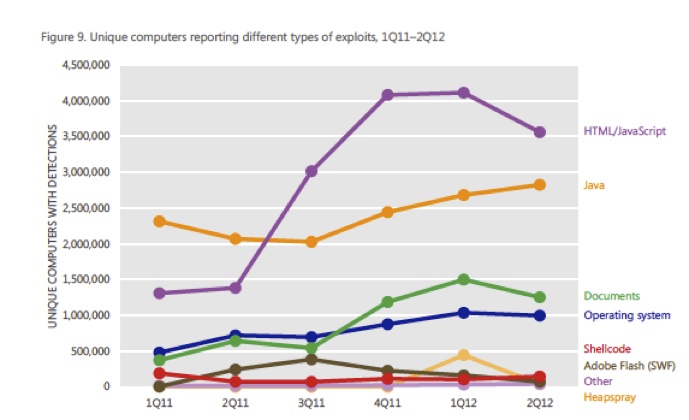
The impact of Black Hole can be tracked using a variety of metrics in the SIR. First, the Microsoft analysis indicates Black Hole as being one of the leading sources of exploits observed by end-user machines. Figure 9 (below) from the report shows a massive increase in the number of HTML/JavaScript over the past year, which was “primarily driven by the continued prevalence of Blacole”. Of interest, Black Hole has become the leading source of end-user exploits, and without an obvious drop in other categories. In short, these are additional new exploits in the wild.
Microsoft Security Intelligence Report Volume 13
In addition to leading the charge in exploits, Black Hole was a leading source of malware infections as well. The Microsoft analysis used a set of six tracking files to identify user machines that had participated in the insecure download of movies, music and applications. When the researchers analyzed these users it was found that Black Hole was one of the leading malicious sources of additional malware infection, second only to Win32/Autorun worms.
This analysis provides some hard numbers to support what many in the industry have observed over the past few years. Namely that the life of exploits and malware are increasingly inter-related, and that the web is increasingly the vector of choice for delivering malware. This underscores the need to extend malware controls to any and all networked applications, and not just email.
Secondly, this supports the notion that IT teams need to incorporate this information into how employees are trained. Many employees are trained on the basics of how to identify phishing attempts, and not to open untrusted attachments. However, in the case of Black Hole, the user likely will never see a file at all. They will simply visit a page and the exploit and resulting malware download will happen in the background. While network-based IPS, anti-malware and drive-by-download protection should be used as security controls, employees also need to know that there are direct consequences to even visiting high-risk websites, such as sites that provide free downloads of media and applications.
Ultimately, the shift of malware to the web requires us to update our thinking both as users and security architects. The data shows that the change is already well underway, and now it is up to us in the industry to make sure users are protected.
Related: Black Hole Exploit Kit Gets an Upgrade
Related: Oracle Java Vulnerability Exploit Rolled into BlackHole Kit













