Attack Traffic Originating from The United States Jumped Nearly 37% in Q4 2011, Says Akamai Report.
Internet infrastructure giant Akamai Technologies, released its Fourth Quarter, 2011 State of the Internet report on Monday which provides insights into global statistics including Internet penetration, mobile traffic and data consumption, connection speeds, and Internet attack traffic.
During the fourth quarter of 2011, Akamai said more than 628 million unique IP addresses from 236 countries and regions connected to its massive global network, giving the company a solid look at what’s happening across the Internet globally.
 According to the report, during the quarter, China generated the most attack traffic at 13 percent, up from 8.6 percent of total attack traffic the company observed in the previous quarter. While fingers often point to China as the “bad guys” of the Internet, the United States is not far behind, and saw a significant jump in attack traffic orginating from U.S.-based IPs. During the quarter, the United States was responsible for 10 percent of attack traffic witnessed, up from 7.3 percent in Q3 2011, representing a spike of nearly 37 percent. Indonesia, which previously held the top spot, came in third at 7.6 percent.
According to the report, during the quarter, China generated the most attack traffic at 13 percent, up from 8.6 percent of total attack traffic the company observed in the previous quarter. While fingers often point to China as the “bad guys” of the Internet, the United States is not far behind, and saw a significant jump in attack traffic orginating from U.S.-based IPs. During the quarter, the United States was responsible for 10 percent of attack traffic witnessed, up from 7.3 percent in Q3 2011, representing a spike of nearly 37 percent. Indonesia, which previously held the top spot, came in third at 7.6 percent.
What’s important to note, is that while Akamai has a global network of more than 100,000 servers, these servers are not all used to gather statistics used in the report related to attack traffic.
“Akamai has a set of unadvertised ‘honeypot’ systems whose purpose is to listen for attempts to connect,” David Belson, director of market intelligence at Akamai, previously told SecurityWeek. “Because these systems are unadvertised, and are separate and distinct from our production service platform, they should not be seeing any sort of attempts to connect on any port. These connection attempts are classified as attack traffic. We record the IP address that is attempting to connect, and use our EdgeScape IP geo-location technology to identify the country where that IP address is located.”
 Overall, the total observed attack traffic aggregated by region shows that Asia Pacific/Oceania generated 45 percent of such attack traffic, Europe 33 percent, the Americas less than 20 percent.
Overall, the total observed attack traffic aggregated by region shows that Asia Pacific/Oceania generated 45 percent of such attack traffic, Europe 33 percent, the Americas less than 20 percent.
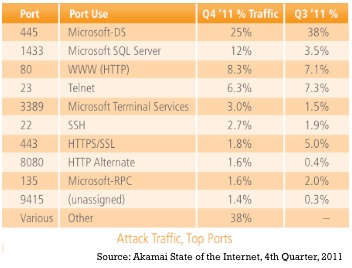
In terms of top ports targeted, Port 8080 (HTTP Alternate) replaced Port 4899 (Remote Administrator) among the top 10. Port 445 remained the target of an overwhelming majority attacks across Akamai’s network as compared to other ports in the top 10.
Other interesting takeaways from the State of the Internet Report include:
• The top 10 ports accounted for 62% of the attack traffic observed
• Attacks targeting Port 1433 (Microsoft SQL Server) grew by more than 3x quarter-over-quarter
• Attacks targeting Ports 8080 and 9415 increased by over 4x as compared to the third quarter
• Port 445 (Microsoft-DS) ended 2011 at the top of the list being targeted by 25 percent of observed attack traffic.
Akamai explained that Port 8080 can be associated with vulnerabilities in Cisco’s Unified Communications Manager and Cisco Unified Contact Center Express products, as well as in unpatched or unsecured JBoss Application Servers, each what could represent high profile targets.
Akamai, which identified attack traffic coming from 187 unique countries/regions, said that geographic location seems to play a role in frequency of observed attacks on specific ports. For example, Port 23 (Telnet) was a top choice for attacks originating from South Korea and Turkey, where it accounted for more than 5x the number of attacks targeting the next most popular port 445 in both countries. For attacks originating from China, Port 1433 (Microsoft SQL Server) seemed to be the top target, in and Port 80 (WWW/HTTP) for Indonesia.
The volume of encrypted traffic that passes through Akamai’s network provides them with a unique perspective on the client-side SSL ciphers being used.
According to the report, SSL ciphers remained consistent with what Akamai saw in prior quarters. On a positive note, the report said the use of more secure ciphers AES256-SHA-1 and AES128-SHA-1, both increased slightly during Q4 2011, with AES256-SHA-1 growing from 47.9% to 48.7%, and AES128-SHA-1 growing from 32.5% to 33.4%. The use of DES-CBCSHA-168, RC4-SHA-128, and RC4-MD5-128 all declined, dropping 15%, 7.5%, and 5.6% respectively, the report added.
In addition to providing insight into potentially malicious attack traffic, Akamai noted that during Q1 2011, 27 percent of the connections to its platform were made at high broadband speeds over 5 Mbps. South Korea had the highest broadband adoption with 83 percent of the country’s connections to Akamai above 5 Mbps. Seven of the top 10 countries for high broadband adoption were in Europe. The United States ranks twelfth at 44 percent.















