Akamai Technologies has released its State of the Internet report for the first quarter of 2012, based on data collected from its massive global network. While Akamai observed attack traffic originating from 182 unique countries, the highest level of observed attacks originated in the Asia-Pacific region over the quarter, the report found.
 More than 42 percent of observed attacks in the first quarter 2012 originated in the Asia Pacific/Oceania region, a slight drop from 45 percent observed in the fourth quarter of 2011. Attack traffic originating in Europe accounted for 35 percent; North & South America accounted for 21 percent; and just under 1.5 percent came from Africa, according to the report. There were slight increases in attack traffic from Europe and the Americas compared to the fourth quarter.
More than 42 percent of observed attacks in the first quarter 2012 originated in the Asia Pacific/Oceania region, a slight drop from 45 percent observed in the fourth quarter of 2011. Attack traffic originating in Europe accounted for 35 percent; North & South America accounted for 21 percent; and just under 1.5 percent came from Africa, according to the report. There were slight increases in attack traffic from Europe and the Americas compared to the fourth quarter.
China was again the top originator of attack traffic, with 16 percent, compared to the fourth quarter’s 13 percent. The United States was next, with 11 percent of observed attack traffic, and Russia at 7 percent. Attack traffic from Turkey, Romania and Germany increased this quarter, while traffic from Taiwan, South Korea, and Brazil declined.
Nearly 75 percent of the observed denial of service attacks were primarily sourced from networks in the Americas and targeted American companies, the report found. About 17 percent of attacks originated in Europe and the Middle East, not only against EMEA companies, but also targeting sites based in other regions. While the Asia/Pacific region had the smallest percentage of denial of service attacks, Akamai expects “the volume and severity of attacks from the region to increase over time,” according to the report.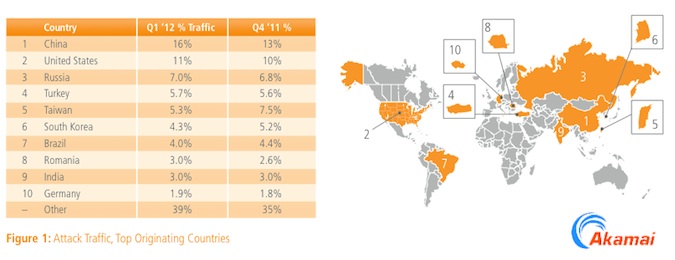
Attackers are moving up the network stack as purely network layer volumetric attacks have less impact on the Internet’s infrastructure, Akamai wrote. Denial-of-service attack tools requiring lower traffic volumes, such as hasdos and slowloris have become more widely used, Akamai said.
Attacks against port 445 (Microsoft DS), 23 (telnet), 80 (HTTP, web), 1433 (Microsoft SQL Server), 3389 (Microsoft Terminal Services), 22 (SSH), 135 (Microsoft RPC), 4899 (remote administrator), 5900 (virtual network computer), and 3306 (MySQL) accounted for 77 percent of observed incidents, according to the report.
The increase was largely attributable to significant growth in port 445 attacks. Port 445 is associated with the Conficker worm.
“Despite patches issued by Microsoft and mitigation activities by the Conficker Working Group, it appears that the worm/botnet is still actively infecting user systems,” Akamai said, noting that the latest Microsoft figures indicates Conficker infected or tried to infect 1.7 million computers running Windows operating systems in the fourth quarter of 2011.
There are also some geographic trends. Akamai found the seven of the top 10 countries generating attack traffic used port 445. Port 23 was the most targeted port in South Korea and Turkey, and second most targeted in Russia and Taiwan, suggesting that attackers were trying to exploit default or common passwords to gain access to a system.
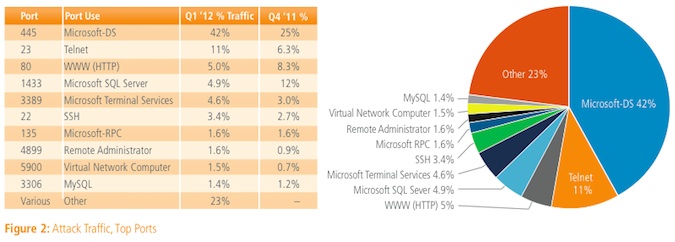
Port 80 was the second-most targeted port in the United States, Germany, and Brazil, “likely indicating that attackers were searching for the presence of Web-based applications with known vulnerabilities that could be exploited to gain control of the system or to install malware,” the report said. In Russia and Taiwan, Port 23 was the second-most targeted port, likely.
The most common vector has been SQL injection attacks, according to the report.
Due to the large number of HTTPS (Port 443) requests that Akamai serves up across its massive network, a number that is upwards of millions of requests per second, Akamai has a unique perspective on the client-side SSL ciphers being used across the Web. According to the report, AES128-SHA-1 and RC4-MD5-128 both saw increases, while usage of the all other ciphers declined.
“In prior quarters, usage of AES256-SHA-1 generally increased, while usage of RC4-MD5-128 generally decreased,” the report noted. “It is not clear why observed usage of AES256-SHA-1 dropped from 48.6% to 44.8% over the course of the quarter—the decline is not of significant concern, as the cipher is still the most widely used and, together with AES128-SHA-1, accounts for nearly 85% of the ciphers presented to Akamai servers.”
While Akamai has a global network of more than 100,000 servers, these servers are not all used to gather statistics used in the report related to attack traffic.
“Akamai has a set of unadvertised ‘honeypot’ systems whose purpose is to listen for attempts to connect,” David Belson, director of market intelligence at Akamai, previously told SecurityWeek. “Because these systems are unadvertised, and are separate and distinct from our production service platform, they should not be seeing any sort of attempts to connect on any port. These connection attempts are classified as attack traffic. We record the IP address that is attempting to connect, and use our EdgeScape IP geo-location technology to identify the country where that IP address is located.”














